Prioritize using Age, RTI, and Attack Surface
Qualys offers you an option to prioritize and remediate vulnerabilities based on filters like Age, Real-Time Threat Indicators (RTI), and Attack Surface.
Prerequisite: Before you start generating
the VMDR Prioritization report, ensure that:
- You have gathered the vulnerability posture for the assets. You
could build your asset inventory using Cloud Agents or other methods such
as Scanners, Passive Sensor, Cloud Inventory, Container Inventory, Mobile
Device Inventory. Learn more
- You have the Create Report global permission for your user role. Contact
your manager if you do not have the adequate permissions.
Perform the following steps to generate Prioritize report using Age, RTI, and Attack surface parameters:
1. In the Prioritization tab click Reports.
2. Click Start Prioritizing.
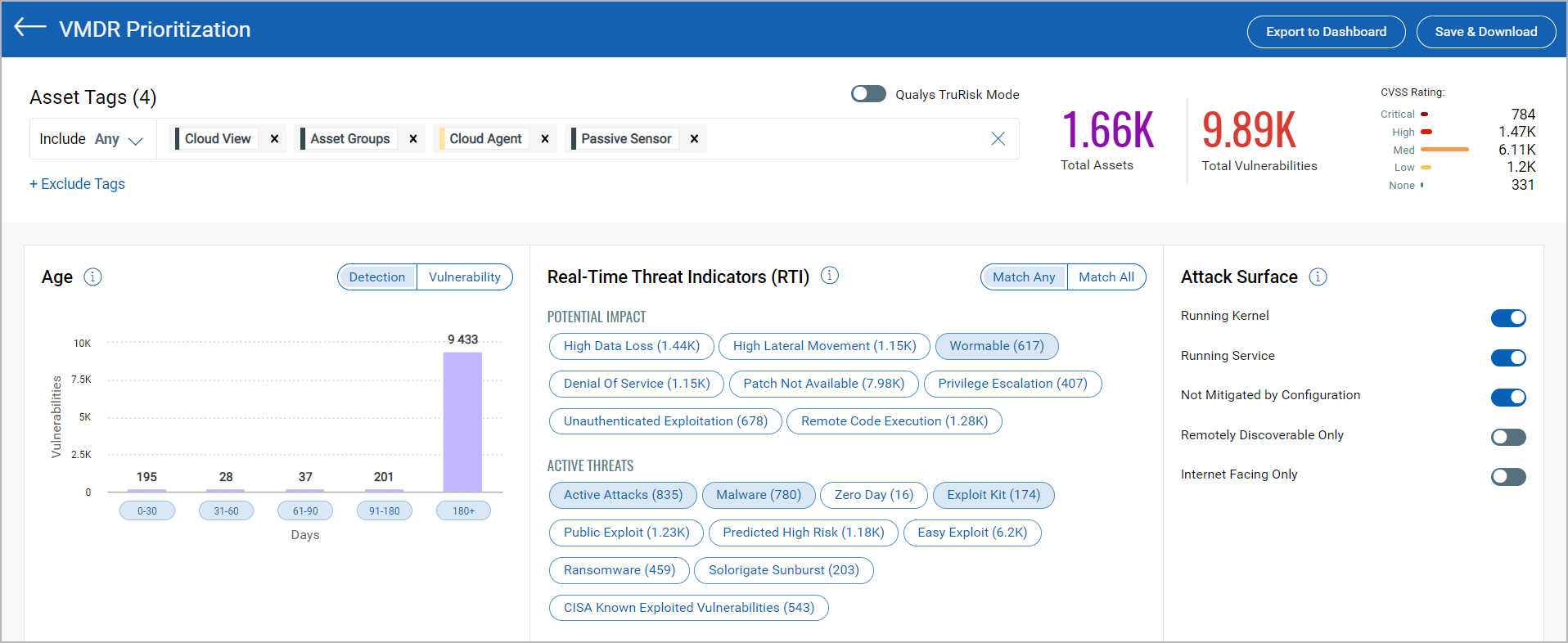
3. Select at least one Asset tag to display the prioritized list of vulnerabilities associated with the assets.
4. Click ![]() to proceed with Prioritization. Show
meShow
me
to proceed with Prioritization. Show
meShow
me
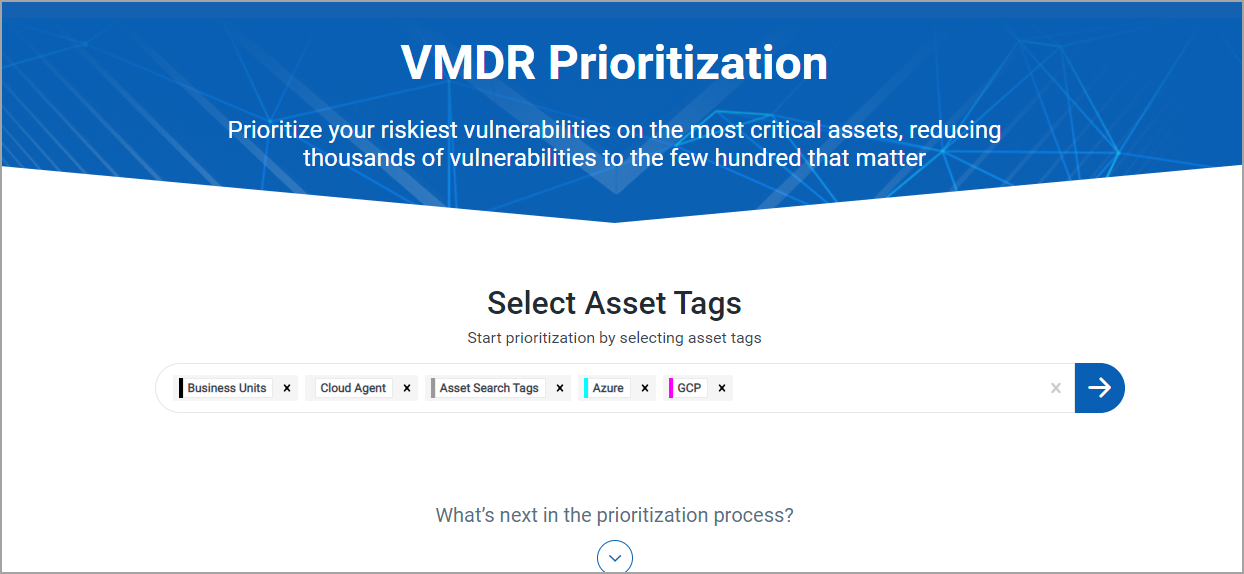
5. In the Asset Tags section, from Include and Exclude menu, select one of the following options:
- Any: to include or exclude all assets that might have any of the selected tags
- All: to include or exclude only those assets which have all the selected tags
6. Select Detection or Vulnerability in the Age bar graph
- Detection: is based on when the vulnerability was first detected (by a scanner or cloud agent). Select detection age ranges (0-30, 31-60, etc.) to include in the report. For example, select 180+ to prioritize vulnerabilities that have been active in your environment the longest.
- Vulnerability: it is the number of days since the vulnerability was disclosed. Select detection age ranges (0-30, 31-60, etc.) to include in the report. For example, select 0-30 to include the vulnerabilities that have been recently disclosed.
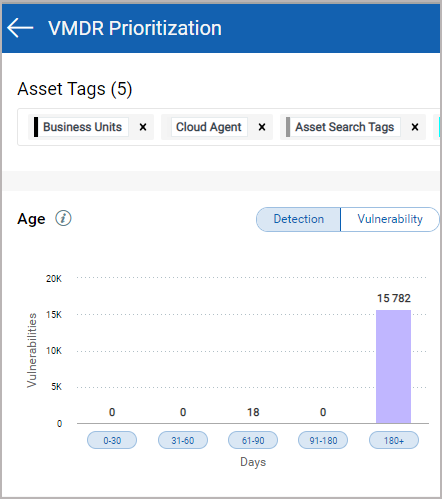
7. In the Real-Time Threat Indicators (RTI) parameter select the indicators from the Potential Impact or Active Threats.
You can toggle between the two options Match Any (logical OR) and Match All (logical AND) for the selected RTI filters.
- Match Any: Vulnerabilities that match at least ONE of the selected RTIs are picked for prioritization. For example, if you opt for Match Any and select three Potential Impact RTIs and two active threats, we prioritize all the assets that are detected with at least one of the five selected vulnerabilities.
- Match All: Vulnerabilities that match ALL of the selected RTIs are picked for prioritization. For example, if you opt for Match All and select three Potential Impact RTIs and two active threats, we prioritize only those assets that are detected with all the five selected vulnerabilities.
For information on each individual RTIs, see the KB article
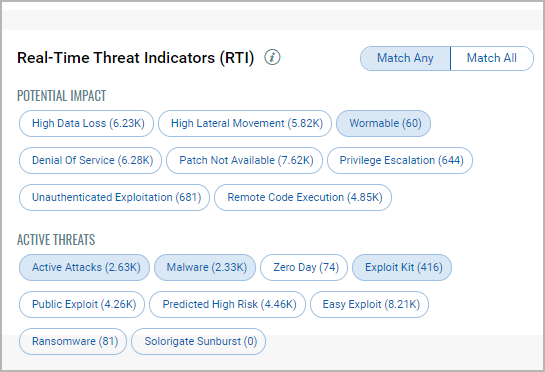
8. In the Attack Surface parameter select the filters to remove vulnerabilities from the report that are not the highest priority.
For information about Attack Surface, see the Attack Vectors
9. Click Prioritize Now to enable the threat intelligence to prioritize the riskiest vulnerabilities on your network for the assets you selected.
Once you generate the report, you could proceed with patching the vulnerabilities (if Patch Management app is enabled in your subscription), export the report in the form of a widget to your dashboard or download the report in CSV format.
Note: A patch job can contain only 50 asset tags in a single job. Ensure that you modify the Prioritization Report for patching the vulnerabilities.