|
|
Web application scans submit forms with the test data that depend on the privileges of the credentials that are used in the authentication record. This can have undesired effects and can potentially impact the data.
To avoid the undesired changes in the target application, we recommend to use one of the following option:
- Use the credentials with read-only access to applications.
- Add configurations for exclude lists, POST data exclude lists, and/or select the GET only method within the option profile.
Keep in mind when these configurations are used instead of test data (credentials with read-only permissions), testing of certain areas of the web application is not included and any vulnerabilities that exist in these areas may not be detected.
These events occur during a scan:
Web Crawling and Link Discovery. We request links and forms, parse HTML for parameter analysis and form values, and interact with the web application. We also extract JavaScript based links and can find custom links. Learn more
Data Analysis. We perform static, off-line analysis of HTTP headers, HTML content and other responses from the web application.
Vulnerability Testing. We perform dynamic, on-line analysis of the web application for a vulnerability scan.
The first time you scan a web application, we recommend you launch a discovery scan. A discovery scan performs information gathered checks only. This is a good way to understand where the scan will go and whether there are URIs to be added to the exclude list for vulnerability scans. For a discovery scan:
- No vulnerability checks are performed.
- Sensitive content checks are performed and findings are reported in your scan results.
- Information gathered checks are performed and findings are reported in your scan results.
Vulnerabilities must be identified and eliminated on a regular basis because new vulnerabilities are discovered every day. For example, Microsoft releases advisories and patches on the second Tuesday of each month – commonly called ‘Patch Tuesday’. We recommend you schedule your scans to run automatically (daily, weekly, monthly). That way you'll always have the current vulnerability information for your web applications.
Go to Detections > Detection List to see the vulnerabilities detected by scans on your web applications. This gives you an easy way to review the vulnerabilities detected on web applications in your account without running reports. Use the search and filtering options (on the left) to take actions on one or more detections.
WAS supports basic security testing of SOAP based web services that have a Web Service Description Language (WSDL) file within the scope of the scan. If WAS identifies a WSDL file that describes web services that are within the scope of the scan, WAS will attempt to perform XSS and SQL injection testing of the web services. Check out this article to learn more.
From the Community: WAS Security Testing of Web Services
You can opt in to receive an email notification each time a scan in your account is completed. Just turn on the Scan Complete Notification in your account settings. Go to the VM application, select User Profile below your user name (in the top right corner). In the user wizard, go to the Notification Options, select "Scan Complete Notification" and be sure to save your account. Once you've turned on the Scan Complete Notification you will receive an email notification each time a WAS scan in your account is finished. In case of multi-scan, you could configure the frequency of notification email to be sent on completion of multi-scan. You could choose to send email after every scan is completed in multi-scan or completion of all scans in a multi-scan. Learn more
Yes, you can do this by configuring exclusion lists in your web application settings. Exclusion lists are exclude lists and allow lists that tell us which links in a web application to scan and which to ignore. You can define either one or both kinds of lists for a web application. Learn more
What if I use an exclude list and an allow list?
What if I use only a exclude list?
The crawl scope options you choose in your web application scan settings determine where the scan will go. You can limit crawling to the URL hostname, content at or below a URL subdirectory, the URL hostname and a specified sub-domain, or the URL hostname and specified domains. Learn more
Yes. To scan a REST API, enter the URL of the Swagger file in the target definition field on the Asset Details panel. Swagger version 2 and OpenAPI version 3 (JSON format) are currently supported. Alternatively, you can provide a Postman Collection to scan your REST API, which is done on the Application Details panel.
From the Community: API Testing with Swagger / OpenAPI and API Testing with Postman Collections
As part of the web application settings, you can upload Selenium scripts. You can use Qualys Browser Recorder to create a Selenium script and then record and play back web applications functions during scans. For each web application in your account, you can create scripts to configure authentication and crawling. Learn more
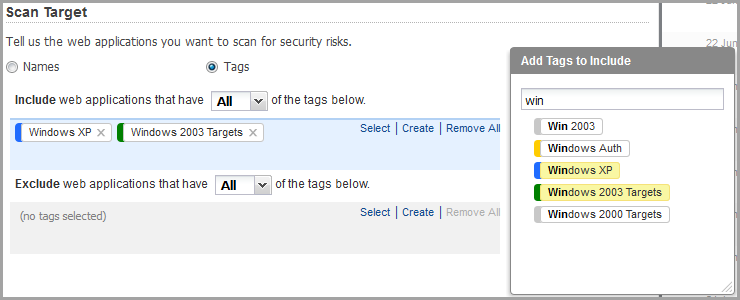
Choose Tags option in the Scan Target section and then click the Select link in the Include web applications section. The tag selector appears with your most recent tags and favorite tags displayed for your convenience. To find a tag, begin typing the tag name in the Search field. The service will dynamically display tags that match your entry. Click a tag to select it. Click outside the tree to add the selected tags. The example below shows the tags Win2003 and Windows XP selected. Show me
Select "All" to include web applications that match all of the tags listed. Select "Any" to include web applications that match at least one of the tags listed. For example, let's say you've selected tags US-West Coast, Windows XP and Port80. If you pick All then only web applications that have all three tags will be included. If you pick Any then web applications that have at least one of the tags will be included.
Add tags to the "Exclude" section. For example, you might include a tag called US-West Coast and exclude the tag California. Any web application that has the California tag will be excluded from the scan even if it also has the US-West Coast tag.
The option profile, along with the web application settings, determines the depth of the scan. If you're not sure which options to use, start with the default profile. We provide "Initial WAS Options" to get you started. This profile has the most common settings and should meet most of your needs.
By creating your own profile, you can fine tune settings like vulnerabilities included (for a vulnerability scan), form submission, number of links to crawl, and password bruteforcing.
We'll perform various security checks depending on the scan type (vulnerability or discovery) and the option profile settings. Want to limit the vulnerability checks for your scan? Just create a custom option profile for your scan.
- Vulnerability checks (vulnerability scan). These include checks for cross-site vulnerabilities (persistent, reflected, header, browser-specific) and SQL injection vulnerabilities (regular and blind).
- Sensitive content checks (vulnerability scan). These include checks for Social Security number (United States), credit card numbers and custom defined.
- Information gathered checks (vulnerability and discovery scan). These collect information about the web application and this gives you scan diagnostics, the links crawled, external links discovered, external form actions discovered, information about the host.
Authenticated scanning is an important feature because many vulnerabilities require authenticated scanning for detection. To perform authenticated scanning, you need to set up authentication records in your web application settings with login credentials. (You can set up multiple records for your web application.) When launching a scan, you'll choose an authentication record for the web application you're scanning.
You can troubleshoot most scan problems by viewing the QIDs in the scan results. Learn more
External scanning is always available using our cloud scanners set up around the globe at our Security Operations Centers (SOCs). For this option, choose External from the Scanner Appliance menu in the web application settings.
Internal scanning uses a scanner appliance placed inside your network. Select the Individual option and choose the scanner appliance by name from the Scanner Appliance menu in the web application settings. Select Tags option to assign multiple scanner appliances (grouped by asset tags). If you don't already have one, contact your Account Manager. Learn more
Yes, scanners must be able to reach the web applications being scanned. Go to Help > About to see the IP addresses for external scanners to whitelist.
Problems can arise when the scan traffic is routed through the firewall from the inside out. That is when the scanner appliance is sitting in the protected network area and scans a target that's located on the other side of the firewall. Learn more
By setting a locked scanner for a web application, the same scanner will be used to scan the web app even if you change the locked scanner sometime in the future. You can set a locked scanner for a web application using the web application wizard - just choose the option "Lock this scanner appliance for this web application".
Changing the locked scanner setting may impact scan schedules if you've already defined them for the web application. We'll notify you if there are schedule conflicts at the time of the change and you can choose to update them to use the new locked scanner if you wish - by default we won't update the schedules.