You can scan Unix-based systems like Citrix NetScaler and F5 using Unix authentication.
How to tell which systems can be scanned with authentication
Start by searching the KnowledgeBase to find all QIDs related to the device or technology you're interested in. Then look at the icons next to each vulnerability title to find out if authentication is required to detect it and the type of authentication needed.
In this example, we searched for QIDs with "citrix netscaler" in the title.
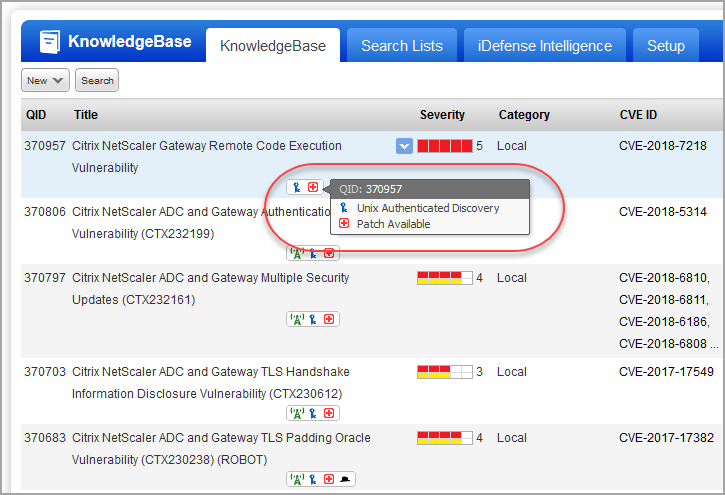
Check out the icons next to each vulnerability title. Mouse over these icons to get more information.
 - This means the vulnerability can be detected using authenticated scanning. The type of authentication needed appears in the mouse-over text. For QID 370957, Unix authentication is required so you'll need a Unix record to scan for this QID.
- This means the vulnerability can be detected using authenticated scanning. The type of authentication needed appears in the mouse-over text. For QID 370957, Unix authentication is required so you'll need a Unix record to scan for this QID.
 - This means the vulnerability can be detected using remote (unauthenticated) scanning.
- This means the vulnerability can be detected using remote (unauthenticated) scanning.
There are several other icons that give you important vulnerability information like whether a patch is available from the vendor and if there's exploit information.