Password auditing on Windows and Unix systems is available using PC. We provide password auditing controls for identifying 1) user accounts with empty passwords, 2) user accounts with the password equal to the user name, and 3) user accounts with passwords equal to an entry in a user-defined password dictionary.
|
Some things to consider... |
|
What are the password auditing controls?What are the password auditing controls? We provide these controls for password auditing: CID 3893 -- Identifies user accounts with empty passwords. CID 3894 -- Identifies user accounts where the password is equal to the user name. CID 3895 -- Identifies user accounts where the password is equal to an entry in the user-defined password dictionary. You configure the password dictionary in a compliance profile, and then apply that profile to your scan task. |
|
How is password information collected?How is password information collected? We use a Dissolvable Agent to collect user password information from target Windows hosts when this information is not accessible remotely. During the scan process the Agent is installed as needed. Once the scan is complete, the Agent removes itself completely. |
|
A few things you need... |
|
Accept the Dissolvable AgentAccept the Dissolvable Agent The Dissolvable Agent must be accepted for your subscription. Go to Scans > Setup > Dissolvable Agent and check to be sure the Agent is accepted. If not, a Manager must accept go there and accept the Agent. Learn more |
|
Configure scan settingsConfigure scan settings Password Auditing controls are not included in compliance scans by default. Go to PC > Scans > Option Profiles, and make the following settings in your option profile before scanning. - Enable the Dissolvable Agent - Enable Password Auditing - Click Configure to create a password dictionary. This is used when evaluating control ID 3895, which identifies user accounts where the password is equal to an entry in the password dictionary. How does it work?How does it work? When evaluating control ID 3895, we compare user account passwords discovered during the compliance scan to the passwords listed in the password dictionary. If a match is found, the control fails. If no match is found, the control passes. |
|
Set up host authenticationSet up host authentication Successful authentication is a requirement for Password Auditing. Create Windows and Unix authentication records for the hosts you want to scan for password auditing controls. Go to PC > Scans > Authentication Records. |
|
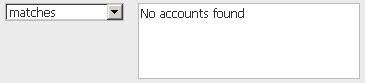
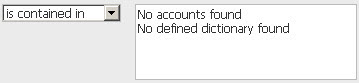
Add password auditing controls to your policyAdd password auditing controls to your policy Add the 3 password auditing controls (Control IDs 3893, 3894 and 3895) to your compliance policy. For CIDs 3893 and 3894, the default expected value in the policy is:
The control will pass if no user accounts are found to violate the control. The control will fail if at least one user account is found to be in violation. For CID 3895, the default expected value in the policy is:
The control will pass if no user accounts are found to violate the control or a password dictionary was not included in the profile used during the scan. The control will fail if at least one user account is found to be in violation. |
|
I'm ready to start password auditing. What are the steps? |
|
Start your compliance scanStart your compliance scan Go to PC > Scans and select New > Scan (or Schedule Scan). Enter your scan settings and click Launch. Be sure to choose an option profile with the Password Auditing option selected. |
|
Check out your scan resultsCheck out your scan results How do I know when the scan is done? You'll know when the scan status shows "Finished". At this time you can select View from the Quick Actions menu to see the full results in an HTML report. If you have notifications turned on you'll get an email. How do I know if authentication worked? We recommend that you verify authentication worked as expected. Learn more When can I run reports? We'll merge (process) your scan
results into your account. Watch for the solid green circle
|
|
Create compliance reportsCreate compliance reports Create compliance reports to compare the data gathered on your hosts during your compliance scan to the expected values defined in your compliance policy. A password auditing control fails when one or more user accounts are found in violation of the control. Each user account that violates the control appears in the Actual field of your report. Go to PC > Reports > New > Compliance Report and choose one of the reports. |