Every completed scan has a scan results report with the raw, unfiltered results.
Check out this video:
Go to VM/VMDR > Scans, identify the scan you're interested in and select View from the Quick Actions menu.
By selecting Download from the Quick Actions menu you can save a copy locally in one of many formats.
Scan results in XML: Qualys API (VM, PC) User Guide ![]()
Yes. Choose View from the Quick Actions menu for your running scan. The scan status appears and partial results are available in an HTML report for the IPs that have been scanned. You can look at the results but you can't run reports on the data until the scan is finished and the results have been processed.
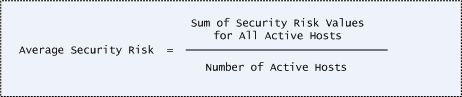
You'll see the average security risk score for all active hosts in the scan results report in the Summary of Vulnerabilities section. The average security risk is calculated as the sum of the security risk scores for all active hosts divided by the number of active hosts. (This calculation method applies to the averages security risk in scan results.)
What is the security risk for each active host?What is the security risk for each active host?
This is the highest severity level detected on the host. For example, if the highest severity on a host is 4 (whether confirmed or potential), then the security risk for the host is 4. Information gathered severity levels are not used.
What are active hosts?What are active hosts?
These are hosts alive at the time of the scan and visible to the user viewing the scan results. Hosts with no vulnerabilities or potential vulnerabilities are counted as active hosts.
Show me the formulaShow me the formula
This formula is used for calculating the average security risk.
You'll see each scanned host identified by IP address with additional information (if collected during the scan):
IP address (DNS hostname, NetBIOS hostname) Operating System
For each host, you'll see the detected vulnerabilities by severity level - confirmed vulnerabilities, potential vulnerabilities and information gathered. Disabled vulnerabilities will appear grayed out.
You'll see a list of hosts that were scanned and not scanned in the Appendix section of your scan results. A host may not be scanned for a variety of reasons.
Show me reasons a host may not be scannedShow me reasons a host may not be scanned
1) The scan was paused. Scans may be paused by a user, by an administrator or automatically by the service as specified in scheduled scan settings. Simply resume the paused scan from the scan history list.
2) The scan was canceled. Scans may be canceled by a user, by an administrator or automatically by the service as specified in scheduled scan settings.
3) The hosts were excluded. Hosts may be excluded on a per scan basis (by the user launching or scheduling the scan) or globally for all scans. Managers and Unit Managers have privileges to edit the global excluded hosts list for the subscription.
4) The hosts were not "alive" at the time of the scan, meaning that they did not respond to probes sent by the scanning engine, and the option to Scan Dead Hosts was not enabled.
5) Hosts were scanned but they could not be reported because the NetBIOS or DNS hostname, whichever tracking method is specified for each host, could not be resolved.
6) The scan was abruptly discontinued. This is a rare occurrence that may be caused for various reasons. If your scan results include hosts in this appendix, contact Support for assistance.
7) Live hosts were not scanned for SCAP compliance because the hosts were found to have a different technology than the technology defined in the SCAP policy (CPE mismatch). An SCAP policy is defined for only one technology.
Hosts that fail authentication appear in the Appendix section of your results. We recommend you run the Authentication Report to get information to help you with troubleshooting the issue before you launch new scans. Go to Reports > Reports and choose New > Authentication Report.
The Operating Systems Detected graph will be empty if your scan did not include "Operating System Detected" vulnerability (QID 45017). The Services Detected graph will be empty if your scan did not include "Open TCP Services List" (QID 82023) and "Open UDP Services List" (QID 82004). Check the option profile you selected for the scan to be sure these QIDs are selected.
Large reports are divided into segments of IPs to make the results more manageable. Use the View menu to see the available segments, and then select a segment and click Go to see the results for that segment.
Tip: Create a scan report with fewer hosts using a report template that filters the output by asset groups or tags. This will make your scan results more manageable for reviewing and sharing with others. You can do this by going to VM/VMDR > Reports > Templates. There are several templates you can choose from (we recommend the Technical Report or the High Severity Report to begin) and you can change the template to select asset group or tags.
For authenticated scans it's important to verify that authentication was successful. It is recommended that you resolve authentication failures before the next scan. Learn more
We store saved scan results separate from host scan data (also called Automatic data). Host scan data is the normalized data collected from your scan results and this is updated as new scans are completed and scan results are processed. Host scan data provides the most up-to-date information and current security status for each host. This appears throughout the user interface and in Automatic vulnerability scan reports. Learn more
Review the Results section of the QID for the host. This will show you the specific reasoning why the vulnerability was reported for that host. Learn more